 Somewhat unsurprisingly, the movies have painted a highly inaccurate picture of the power of polygraphs, or so-called lie-detector tests. While many crime dramas showcase a seemingly miraculous technology for distinguishing truths from lies, this portrayal, itself, is far from true.
Somewhat unsurprisingly, the movies have painted a highly inaccurate picture of the power of polygraphs, or so-called lie-detector tests. While many crime dramas showcase a seemingly miraculous technology for distinguishing truths from lies, this portrayal, itself, is far from true.
However, a new study published in the Journal of Clinical Psychiatry suggests that polygraph tests may yet have a role to play, alongside MRI machines and brain scans.
Subjects were asked to write down numbers and then lie to researchers about what they had written down. While being interrogated, each participant was subjected to both an MRI scan and a polygraph test, and the researchers attempted to evaluate when they were being lied to.
While the MRI test proved to be about 24 percent more effective than the polygraph, both tests employed in tandem were able to determine deception in almost every case: a remarkable achievement.
Previous studies on MRI testing found them to be up to 90 percent accurate, while the accuracy of polygraph tests ranged wildly from perfectly accurate to completely unreliable. Even 90 percent accuracy falls short of being reliable enough for criminal proceedings. However, with this study, the doors have opened towards justifying more research into lie detection testing.
As Dr. Daniel Langleben, a study author, said: “While the jury remains out on whether fMRI will ever become a forensic tool, these data certainly justify further investigation of its potential.”
In order to appreciate the significance of this study, it is important to understand the limitations that both MRI machines and polygraph tests face in detecting deception.
MRI machines generate images of the subjects’ brains. These images allow researchers to see any physical abnormalities or changes in blood flow, revealing which parts of the brain are currently active. Some of the earliest studies on MRIs as lie detectors had subjects select playing cards and then lie about which ones they had picked. This helped narrow down which parts of the brain light up when a person is being deceitful.
However, there may be confounding factors, as these MRI images often just reveal when the subject has to think quickly about how best to respond. While this does detect lies, it may also indicate uncertainty, or it could be easily misled by a well-rehearsed story that took no effort to recite.
Based on this uncertainty, every attempt to introduce MRI-based lie detection as evidence in court proceedings has failed. In fact, they often show false signs of deception, which would be a major flaw in court proceedings.
Polygraph tests, on the other hand, work by tracking the subject’s heart rate, blood pressure, respiration, and other physiological responses. Law enforcement personnel ask “control” questions that are only tangentially related to the investigation at hand, as well as “relevant” questions which probe for details on the subject’s involvement in the crime.
If the subject shows a higher heart rate when asked the “relevant” questions, this indicates that they are attempting to conceal their guilt. However, there are significant underlying problems with this approach. In fact, there is little evidence to show that these physiological responses are even unique to the practice of deception.
Between the theoretical flaws and the fact that polygraphs can be outsmarted, it is understandable that they are currently not admissible in court proceedings.
For more information on polygraph tests, read our blog here. Also, check out this post to learn how you can be a better lie-detector.
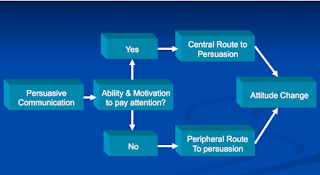 Figure 1: Elaboration-Likelihood Model (Petty & Cacioppo, 1979)Indeed, the specific emotions of disgust and fear have been shown as effective in behaviour change through numerous studies covering several domains. For example, Evans et al. (1970) presented junior high school students with persuasive appeals regarding teeth cleaning. They received one of five types of persuasive appeal: High fear, lower fear and positive were all followed by specific recommendations; the fourth involved only specific recommendations and the fifth involved an elaboration of the specific recommendations. It was found that although positive communication resulted in greater information retention, high and low fear groups reported stronger intentions to behave than the positive and elaboration groups. In addition, the high fear appeal group showed greatest reported behaviour change, measured by reported tooth brushing behaviour. However, when assessing actual behaviour change, fear appeals were less effective. Therefore, fear is effective in altering reported behaviour change but not actual behaviour change.
Figure 1: Elaboration-Likelihood Model (Petty & Cacioppo, 1979)Indeed, the specific emotions of disgust and fear have been shown as effective in behaviour change through numerous studies covering several domains. For example, Evans et al. (1970) presented junior high school students with persuasive appeals regarding teeth cleaning. They received one of five types of persuasive appeal: High fear, lower fear and positive were all followed by specific recommendations; the fourth involved only specific recommendations and the fifth involved an elaboration of the specific recommendations. It was found that although positive communication resulted in greater information retention, high and low fear groups reported stronger intentions to behave than the positive and elaboration groups. In addition, the high fear appeal group showed greatest reported behaviour change, measured by reported tooth brushing behaviour. However, when assessing actual behaviour change, fear appeals were less effective. Therefore, fear is effective in altering reported behaviour change but not actual behaviour change. 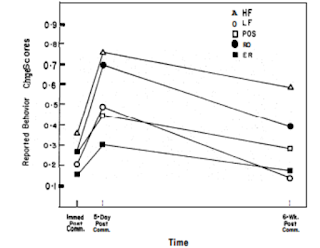 Figure 2 – Reported behaviour change scores (Evans et al., 1970). HF = High fear; LF = Low fear; POS = Positive; RO = Recommendation only; ER = Elaborated recommendation The effectiveness of fear appeals has been further supported through a meta-analysis of over 100 studies (Witte & Allen, 2000). They found that the stronger the fear appeal, the greater attitude, intention and behaviour change. In addition, the greater the severity of the fear message, the greater the persuasion. Perhaps most notably, Witte and Allen found that individual differences did not influence the extent to which the fear appeal was persuasive, hence suggesting when viewing an advert using fear, individuals will use the peripheral route regardless of personality.Finally, the effect of disgust visuals on attitudes towards animal experimentation was investigated by Nabi (1998). Participants were shown a counterargument and rebuttal of either: low disgust/low affect, low disgust/high affect, high disgust/low affect or high disgust/high affect advert, where low disgust showed a monkey lying on a lab table and high disgust showed a monkey being inflicted with severe head injuries. In addition, low affect refers to showing a talking head, whilst high affect involves showing sick babies who might benefit from animal research. It was found that as the level of disgust increased, level of support for animal experimentation decreased, thus suggesting that disgust is an effective way to change attitudes and hence perhaps behaviour. In conclusion, although being subjected to a Corsodyl advert while watching your favourite television show is far from pleasant, it is an effective way of implementing both attitude and behaviour change. An advert such as this utilises emotions like fear and disgust resulting in an individual being persuaded to go out and buy Corsodyl via the peripheral route.ReferencesEvans, R. I., Rozelle, R. M., Lasater, T. M., Dembroski, T. M., & Allen, B. P. (1970). Fear arousal, persuasion and actual versus implied behavioural change: new perspective utilizing a real-life dental hygiene program. Journal of Personality and Social Psychology, 16, 220-227.Hovland, C. I., Janis, I. L., & Kelley, H. H. (1953). Communication and persuasion: psychological studies of opinion change. New Haven: Yale University Press. Nabi, R. L. (2009). The effect of disgust-eliciting visuals on attitudes toward animal experimentation. Communication Quarterly, 46, 572-484.Petty, R. E., & Cacioppo, J. T. (1979). Issue involvement can increase or decrease persuasion by enhancing message-relevant cognitive responses. Journal of Personality and Social Psychology, 37, 1915-1926. Witte, K., & Allen, M. (2000). A meta-analysis of fear appeals: Implications for effective public health campaigns. Health, Education and Behaviour, 27, 591-615.Charlotte Cartwright
Figure 2 – Reported behaviour change scores (Evans et al., 1970). HF = High fear; LF = Low fear; POS = Positive; RO = Recommendation only; ER = Elaborated recommendation The effectiveness of fear appeals has been further supported through a meta-analysis of over 100 studies (Witte & Allen, 2000). They found that the stronger the fear appeal, the greater attitude, intention and behaviour change. In addition, the greater the severity of the fear message, the greater the persuasion. Perhaps most notably, Witte and Allen found that individual differences did not influence the extent to which the fear appeal was persuasive, hence suggesting when viewing an advert using fear, individuals will use the peripheral route regardless of personality.Finally, the effect of disgust visuals on attitudes towards animal experimentation was investigated by Nabi (1998). Participants were shown a counterargument and rebuttal of either: low disgust/low affect, low disgust/high affect, high disgust/low affect or high disgust/high affect advert, where low disgust showed a monkey lying on a lab table and high disgust showed a monkey being inflicted with severe head injuries. In addition, low affect refers to showing a talking head, whilst high affect involves showing sick babies who might benefit from animal research. It was found that as the level of disgust increased, level of support for animal experimentation decreased, thus suggesting that disgust is an effective way to change attitudes and hence perhaps behaviour. In conclusion, although being subjected to a Corsodyl advert while watching your favourite television show is far from pleasant, it is an effective way of implementing both attitude and behaviour change. An advert such as this utilises emotions like fear and disgust resulting in an individual being persuaded to go out and buy Corsodyl via the peripheral route.ReferencesEvans, R. I., Rozelle, R. M., Lasater, T. M., Dembroski, T. M., & Allen, B. P. (1970). Fear arousal, persuasion and actual versus implied behavioural change: new perspective utilizing a real-life dental hygiene program. Journal of Personality and Social Psychology, 16, 220-227.Hovland, C. I., Janis, I. L., & Kelley, H. H. (1953). Communication and persuasion: psychological studies of opinion change. New Haven: Yale University Press. Nabi, R. L. (2009). The effect of disgust-eliciting visuals on attitudes toward animal experimentation. Communication Quarterly, 46, 572-484.Petty, R. E., & Cacioppo, J. T. (1979). Issue involvement can increase or decrease persuasion by enhancing message-relevant cognitive responses. Journal of Personality and Social Psychology, 37, 1915-1926. Witte, K., & Allen, M. (2000). A meta-analysis of fear appeals: Implications for effective public health campaigns. Health, Education and Behaviour, 27, 591-615.Charlotte Cartwright Leading the way are the so-called health and wellness bloggers that have all somehow developed a sudden intolerance to gluten, wheat and dairy. A little bit of a coincidence isn’t it?But why do we seem to be falling for this new health craze, with its extortionate prices and bland tastes?As the availability heuristic explains, the things in or mind that are more accessible, the more likely we are to choose them. Agenda setting theory is a form of availability heuristic explaining that it is the News, which influences the perceived importance off things through repetition and emphasis so as soon as we read something, we form a biased opinion of it. Therefore, with hundreds of thousands of followers on every social media outlet, it’s no surprise that an increasing number of people are turning to these bloggers for guidance, making it almost impossible to check your Instagram without being bombarded with some new healthy diet. Yet, it seems bizarre that we automatically trust these bloggers, the majority of whom don’t even hold a qualification in nutrition or fitness. We are prone to judgmental heuristics such as credibility bias in that we assume that these bloggers are experts in the field of health and food, ignoring any arguments and automatically allowing ourselves to be convinced solely by their status (Cialdini, 2009). For instance, how many times have you thought that if something is expensive, it must be a good product? Many times right? This is exactly how we think that ‘if an expert said so, it must be true’. In some cases, they may well be telling the truth, but at other times their advice may cause us to make costly mistakes (especially if you’re on a student budget but can only buy gluten and wheat free edamame spaghetti).
Leading the way are the so-called health and wellness bloggers that have all somehow developed a sudden intolerance to gluten, wheat and dairy. A little bit of a coincidence isn’t it?But why do we seem to be falling for this new health craze, with its extortionate prices and bland tastes?As the availability heuristic explains, the things in or mind that are more accessible, the more likely we are to choose them. Agenda setting theory is a form of availability heuristic explaining that it is the News, which influences the perceived importance off things through repetition and emphasis so as soon as we read something, we form a biased opinion of it. Therefore, with hundreds of thousands of followers on every social media outlet, it’s no surprise that an increasing number of people are turning to these bloggers for guidance, making it almost impossible to check your Instagram without being bombarded with some new healthy diet. Yet, it seems bizarre that we automatically trust these bloggers, the majority of whom don’t even hold a qualification in nutrition or fitness. We are prone to judgmental heuristics such as credibility bias in that we assume that these bloggers are experts in the field of health and food, ignoring any arguments and automatically allowing ourselves to be convinced solely by their status (Cialdini, 2009). For instance, how many times have you thought that if something is expensive, it must be a good product? Many times right? This is exactly how we think that ‘if an expert said so, it must be true’. In some cases, they may well be telling the truth, but at other times their advice may cause us to make costly mistakes (especially if you’re on a student budget but can only buy gluten and wheat free edamame spaghetti). 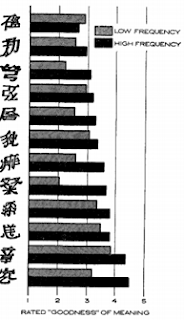 Fig 1. Ratings of ‘goodness’ of Chinese charactersAnother reason is that of mere exposure, as proposed by Zajonc (1968). According to this theory, the more exposed we are to things; the more favourable they are seen. For example, in his study he found that after participants saw a range of made up Chinese characters, the characters they saw more were rated as more ‘good’ compared to characters they saw less .The elaboration likelihood model is a dual process model of persuasion that explains how certain influences can lead to different impacts on a person’s attitudes and behaviours (Li, 2013). There are two possible routes that one may take, the central route, which requires one to take part in systematic, critical and effortful thinking, or the peripheral route, which involves using simple automatic cues without effortful thinking. The more thought and elaboration that goes into making a decision, the more likely it is to trigger stronger attitude and behaviour change (Boyce & Kujjer, 2014). Therefore, in terms of this healthy eating craze, it seems that people who are less motivated may use cues such as one’s perceived credibility in order to arrive at a decision whereas those that are more invested are more likely to have a sustained change in behaviour and stick to ‘clean-eating’. Of course we always want to make sure that we are doing things that other people are, keeping up with trends and not feeling left out. Social influence and in particular, normative social influence plays a major part in how we are persuaded by the behaviour and expectations of others in order to conform to the norm of society (Li, 2013). If all your friends are out there buying almond milk and you purchase the forbidden semi-skimmed, then be prepared to face some serious social segregation. So regardless of our beliefs and attitudes, we are under high levels of social pressure to conform to certain behaviours and before deciding whether to accept and carry out this behaviour ourselves, we first observe successful experiences encountered by others (Li, 2013). As Mcferran, Dahl, Fitzsimons and Morales, (2010) found, when a confederate set up a norm, other participants conformed to the norm so either ate more or less, depending on what the confederate’s norm was. Moreover, as the group size increases, people increasingly conform to the group norm, demonstrating how an anchor set up by others can be highly influential when making our own decisions. I mean if Sophie lost 3 stone by eating apples for a week, then surely it’ll work for me too right?
Fig 1. Ratings of ‘goodness’ of Chinese charactersAnother reason is that of mere exposure, as proposed by Zajonc (1968). According to this theory, the more exposed we are to things; the more favourable they are seen. For example, in his study he found that after participants saw a range of made up Chinese characters, the characters they saw more were rated as more ‘good’ compared to characters they saw less .The elaboration likelihood model is a dual process model of persuasion that explains how certain influences can lead to different impacts on a person’s attitudes and behaviours (Li, 2013). There are two possible routes that one may take, the central route, which requires one to take part in systematic, critical and effortful thinking, or the peripheral route, which involves using simple automatic cues without effortful thinking. The more thought and elaboration that goes into making a decision, the more likely it is to trigger stronger attitude and behaviour change (Boyce & Kujjer, 2014). Therefore, in terms of this healthy eating craze, it seems that people who are less motivated may use cues such as one’s perceived credibility in order to arrive at a decision whereas those that are more invested are more likely to have a sustained change in behaviour and stick to ‘clean-eating’. Of course we always want to make sure that we are doing things that other people are, keeping up with trends and not feeling left out. Social influence and in particular, normative social influence plays a major part in how we are persuaded by the behaviour and expectations of others in order to conform to the norm of society (Li, 2013). If all your friends are out there buying almond milk and you purchase the forbidden semi-skimmed, then be prepared to face some serious social segregation. So regardless of our beliefs and attitudes, we are under high levels of social pressure to conform to certain behaviours and before deciding whether to accept and carry out this behaviour ourselves, we first observe successful experiences encountered by others (Li, 2013). As Mcferran, Dahl, Fitzsimons and Morales, (2010) found, when a confederate set up a norm, other participants conformed to the norm so either ate more or less, depending on what the confederate’s norm was. Moreover, as the group size increases, people increasingly conform to the group norm, demonstrating how an anchor set up by others can be highly influential when making our own decisions. I mean if Sophie lost 3 stone by eating apples for a week, then surely it’ll work for me too right? The theory of planned behaviour can also be used to explain why the masses are following the clean-eating hype. It is based on the foundation that the best predictor of actual behaviour is the behaviour that a person actually intends to carry out. It involves three key components; a person’s attitude towards the specific behaviour i.e. clean-eating, subjective norms, which involves beliefs about what others expect us to do and finally perceived behavioural control, the degree to which a person has control over their own behaviour. If one has more favourable attitudes towards a specific behaviour as well as more favourable subjective norms and greater perceived behavioural control, this strengthens their intentions to perform the behaviour and so they will engage in this clean-eating obsession.So there we have it, don’t join this health fixation if you don’t want to, but there will be enough influences surrounding you to persuade you to do so. After all, who can resist a bit of avocado on toast? References:Boyce, A. J., & Kuijer, G. R. (2014). Focusing on media body ideal images triggers food intake among restrained eaters: A test of restraint theory and the elaboration likelihood model. Eating Behaviors, 15, 262-270.Cialdini, R. B. (2009). Influence: Science and practice. Boston: Pearson Education. Li, C. Y. (2013). Persuasive messages on information system acceptance: A theoretical extension of elaboration likelihood model and social influence theory. Computers in Human Behavior, 29, 264-275. Mcferran, B., Dahl, D. W., Fitzsimons, G. J., & Morales, A. C. (2010). I’ll have What She’s Having: Effects of Social Influence and Body Type on the Food Choices of Others. Journal Of Consumer Research, 36, 915-929. Zajonc, R. B. (1968). Attitudinal effects of mere exposure. Journal of Personality and Social Psychology, 9, 1–27.
The theory of planned behaviour can also be used to explain why the masses are following the clean-eating hype. It is based on the foundation that the best predictor of actual behaviour is the behaviour that a person actually intends to carry out. It involves three key components; a person’s attitude towards the specific behaviour i.e. clean-eating, subjective norms, which involves beliefs about what others expect us to do and finally perceived behavioural control, the degree to which a person has control over their own behaviour. If one has more favourable attitudes towards a specific behaviour as well as more favourable subjective norms and greater perceived behavioural control, this strengthens their intentions to perform the behaviour and so they will engage in this clean-eating obsession.So there we have it, don’t join this health fixation if you don’t want to, but there will be enough influences surrounding you to persuade you to do so. After all, who can resist a bit of avocado on toast? References:Boyce, A. J., & Kuijer, G. R. (2014). Focusing on media body ideal images triggers food intake among restrained eaters: A test of restraint theory and the elaboration likelihood model. Eating Behaviors, 15, 262-270.Cialdini, R. B. (2009). Influence: Science and practice. Boston: Pearson Education. Li, C. Y. (2013). Persuasive messages on information system acceptance: A theoretical extension of elaboration likelihood model and social influence theory. Computers in Human Behavior, 29, 264-275. Mcferran, B., Dahl, D. W., Fitzsimons, G. J., & Morales, A. C. (2010). I’ll have What She’s Having: Effects of Social Influence and Body Type on the Food Choices of Others. Journal Of Consumer Research, 36, 915-929. Zajonc, R. B. (1968). Attitudinal effects of mere exposure. Journal of Personality and Social Psychology, 9, 1–27.