In recent Apple iMessage updates the way links are handled within an SMS message have changed significantly and this adaptation poses quite a security concern for us. Early 2016 we were the first company in the UK to offer SMShing services. These SMS messages are like phishing emails and contain a pretext alongside a link within the message. When a… Read more →
Fighting Phishing Email Scams: What You Should Know
Phishing email scams are more effective than you may think. Read our infographic Don’t Let Phishing Emails Hook Your Employees. By: Brand BarneyWhen you think of social engineering, you may think of someone walking into your business and stealing data from servers, computers, etc. But companies aren’t just getting socially engineered in person; it’s happening online too. Many employees fall victim to phishing email scans, which can lead to potential data breaches and loss of important information.What is a phishing scam?
By: Brand BarneyWhen you think of social engineering, you may think of someone walking into your business and stealing data from servers, computers, etc. But companies aren’t just getting socially engineered in person; it’s happening online too. Many employees fall victim to phishing email scans, which can lead to potential data breaches and loss of important information.What is a phishing scam? Phishing is a type of Internet-based social engineering. Cybercriminals use legitimate businesses and situations to email and convince their victims to give them their personal information such as social security numbers.Some phishing emails will have the victim click on a link, which introduces malware to the user’s device. The malware can then grant access to the attacker, leaving them free to steal sensitive data. Other emails will state that an item you purchased online can’t be shipped because the credit card number wasn’t correct, or the billing address was wrong, etc. They then have you click on a link to a spoofed website and ask for updated payment/shipping information.SEE ALSO: Top 10 Types of Phishing EmailsWhy do phishing email scams work?With all the online scams that are happening, you’d think we’d be more wary of phishing email scams. Yet, these types of scams are responsible for a lot of lost data in companies. Here are some reasons why phishing scams still work:
Phishing is a type of Internet-based social engineering. Cybercriminals use legitimate businesses and situations to email and convince their victims to give them their personal information such as social security numbers.Some phishing emails will have the victim click on a link, which introduces malware to the user’s device. The malware can then grant access to the attacker, leaving them free to steal sensitive data. Other emails will state that an item you purchased online can’t be shipped because the credit card number wasn’t correct, or the billing address was wrong, etc. They then have you click on a link to a spoofed website and ask for updated payment/shipping information.SEE ALSO: Top 10 Types of Phishing EmailsWhy do phishing email scams work?With all the online scams that are happening, you’d think we’d be more wary of phishing email scams. Yet, these types of scams are responsible for a lot of lost data in companies. Here are some reasons why phishing scams still work:![]() TweetWe’re trustingWe’d like to believe the people emailing us are genuine. It’s human nature to want to trust others, especially those that reach out to us. Unfortunately, social engineers take advantage of that and use it to steal from companies.Good phishing emails look officialSome emails can recreate a company logo and make the email look convincing. Just like a social engineer in person looks like they belong in your company, phishing emails look like they are part of the company contacting you.Follow for more data security articles like thisThey prey on our fearWhen we’re scared, we tend to not act logically. Some phishing emails take advantage of that, using scare tactics to cause us to make an impulsive decision. For example, you may receive an email stating that you have had a breach of your personal banking information, and you need to click on a link to log in and change your online banking password. The attacker is banking (pun intended) that you will want to quickly protect yourself or check your online balance to ensure you still have money after the “breach.”SEE ALSO: 7 Ways to Recognize a Phishing EmailHow do you combat phishing email scams?Be skeptical: Always verify everything with the company you are working with, especially if it involves sensitive information. If a banking institution emails you, asking for credit card information, call them from their business phone to verify. Avoid giving important data over email when possible.Train employees: Make sure your employees are aware of phishing emails and what to do if they suspect they’re receiving one. Hold quarterly training meetings, if not monthly.Have policies: Establish procedures employees should follow should they receive a phishing email or anything that seems suspicious. This could include how to verify if an email is legitimate, who to notify, and how to deal with such an email.Let us help you train your employees against phishing!Phishing is easier than you thinkPhishing email scams are more of a danger than many companies realize. And it doesn’t take a particularly skilled attacker to create a successful phishing campaign.Similar to social engineering, phishing targets the company’s weakest link in security: the employees. An untrained employee can inadvertently cause a lot of damage to their company if they fall victim to a phishing campaign.Remember, when it comes to emails, be smart and be careful with sharing your data.Brand Barney (CISSP, HCISPP, QSA) is a Security Analyst at SecurityMetrics, has over 10 years of data security experience, and will totally geek out if you mention Doctor Who. Brand loves to play jazz piano and daydreams about being as great as Dave Brubeck or Thelonious Monk. Connect with him on Twitter or check out his other blog posts.Want to learn more about spotting phishers? Check out the infographic below!
TweetWe’re trustingWe’d like to believe the people emailing us are genuine. It’s human nature to want to trust others, especially those that reach out to us. Unfortunately, social engineers take advantage of that and use it to steal from companies.Good phishing emails look officialSome emails can recreate a company logo and make the email look convincing. Just like a social engineer in person looks like they belong in your company, phishing emails look like they are part of the company contacting you.Follow for more data security articles like thisThey prey on our fearWhen we’re scared, we tend to not act logically. Some phishing emails take advantage of that, using scare tactics to cause us to make an impulsive decision. For example, you may receive an email stating that you have had a breach of your personal banking information, and you need to click on a link to log in and change your online banking password. The attacker is banking (pun intended) that you will want to quickly protect yourself or check your online balance to ensure you still have money after the “breach.”SEE ALSO: 7 Ways to Recognize a Phishing EmailHow do you combat phishing email scams?Be skeptical: Always verify everything with the company you are working with, especially if it involves sensitive information. If a banking institution emails you, asking for credit card information, call them from their business phone to verify. Avoid giving important data over email when possible.Train employees: Make sure your employees are aware of phishing emails and what to do if they suspect they’re receiving one. Hold quarterly training meetings, if not monthly.Have policies: Establish procedures employees should follow should they receive a phishing email or anything that seems suspicious. This could include how to verify if an email is legitimate, who to notify, and how to deal with such an email.Let us help you train your employees against phishing!Phishing is easier than you thinkPhishing email scams are more of a danger than many companies realize. And it doesn’t take a particularly skilled attacker to create a successful phishing campaign.Similar to social engineering, phishing targets the company’s weakest link in security: the employees. An untrained employee can inadvertently cause a lot of damage to their company if they fall victim to a phishing campaign.Remember, when it comes to emails, be smart and be careful with sharing your data.Brand Barney (CISSP, HCISPP, QSA) is a Security Analyst at SecurityMetrics, has over 10 years of data security experience, and will totally geek out if you mention Doctor Who. Brand loves to play jazz piano and daydreams about being as great as Dave Brubeck or Thelonious Monk. Connect with him on Twitter or check out his other blog posts.Want to learn more about spotting phishers? Check out the infographic below!
7 Ways to Recognize a Phishing Email
“You can fool some of the people all of the time, and all of the people some of the time, but you cannot fool all of the people all of the time.” –Abraham Lincoln  By: David EllisAre you sure that email from UPS is actually from UPS? (Or Costco, BestBuy, or the myriad of unsolicited emails you receive every day?) Companies and individuals are often targeted by cybercriminals via emails designed to look like they came from a legitimate bank, government agency, or organization. In these emails, the sender asks recipients to click on a link that takes them to a page where they will confirm personal data, account information, etc.
By: David EllisAre you sure that email from UPS is actually from UPS? (Or Costco, BestBuy, or the myriad of unsolicited emails you receive every day?) Companies and individuals are often targeted by cybercriminals via emails designed to look like they came from a legitimate bank, government agency, or organization. In these emails, the sender asks recipients to click on a link that takes them to a page where they will confirm personal data, account information, etc.
© SecurityMetrics | www.securitymetrics.com/pci | 801.705.5665 |
Hey guys, and welcome back to the SecurityQ, your source for business data security. Today on the SecurityQ, I want to cover one question. Are your employees properly trained to protect your business against phishing attacks? Not that type of fishing! Phishing is another tool used by hackers to gain access to your personal data. Phishing relies on your employees willingness to provide sensitive information like passwords, bank, and tax information. Here’s how it works. Companies are targeted via an email that is designed to look like it comes from a legitimate bank, organization our government agency. Then the sender asks to confirm personal information, in essence, phishing for data. For example. Let’s say your business does e-commerce through Pay Pal. Hackers posing as PayPal will contact you via email asking you to confirm sensitive information pertaining to your account. Once information is obtained, hackers use the credentials gained to steal your sensitive data mostly through attacks like malware and back doors to your network. That’s hook, line, and sinker. The scary thing is, you may have the best technology in the world but if your employees aren’t properly trained, that technology is a complete and utter waste. Currently twenty percent of all breaches now involve phishing. Everyone in every industry and every company is ultimately a target. Keep in mind, it takes only one untrained employees to give away all the data you worked so hard to protect. As a business owner, how can you detect phishing attacks and properly train employees? First the message or email you’re receiving may appear entirely convincing. You should keep a lookout for three things. Layout issues, spelling , and grammatical issues, go hand in hand with phishing attacks. Second don’t just check the name of the person sending email. You need to check the email address and ensure that there are no alterations made to it. For example, additional letters for numbers added to the email address. Last, most companies will never ask for your personal information through email. If there’s any doubt, contact the sender. Remember, even savvy technology users can find themselves fooled by messages that appear authentic so be cautious, Our advice? Educate your employees about phishing attacks. When it comes to staying safe online, it never hurts have a little bit a cynicism. Well guys, that’s all the time we have for today on the SecurityQ, but as always we want to hear from you. So post your questions in the comments below, and don’t forget to subscribe. See ya next time on the SecurityQ.wistiaEmbed = Wistia.embed(“exi3oxmnof”); This technique is called phishing, and it’s a way hackers con you into providing your personal information or account data. Once your info is obtained, hackers create new user credentials or install malware (such as backdoors) into your system to steal sensitive data. SEE ALSO: Examples of common phishing attempts.It’s often difficult to distinguish a fake email from a verified one, however most have subtle hints of their scammy nature. Here are seven ways to help you recognize a phishing email and maintain email security.1. Legit companies don’t request your sensitive information via emailChances are if you receive an unsolicited email from an institution that provides a link or attachment and asks you to provide sensitive information, it’s a scam. Most companies will not send you an email asking for passwords, credit card information, credit scores, or tax numbers, nor will they send you a link from which you need to login. 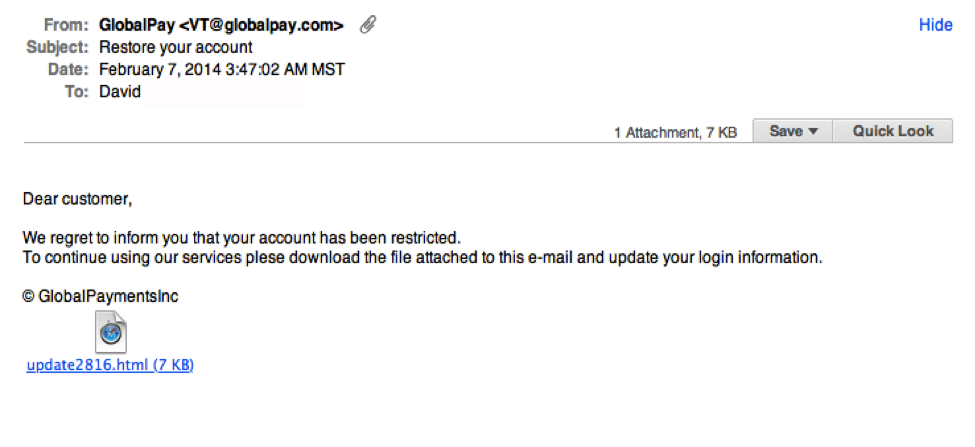 Notice the generic salutation at the beginning, and the unsolicited web link attachment?2. Legit companies call you by your namePhishing emails typically use generic salutations such as “Dear valued member,” “Dear account holder,” or “Dear customer.” If a company you deal with required information about your account, the email would call you by name and probably direct you to contact them via phone.
Notice the generic salutation at the beginning, and the unsolicited web link attachment?2. Legit companies call you by your namePhishing emails typically use generic salutations such as “Dear valued member,” “Dear account holder,” or “Dear customer.” If a company you deal with required information about your account, the email would call you by name and probably direct you to contact them via phone. Sir/Madam? Also, what’s up with the 17 in the middle of the sentence?3. Legit companies have domain emailsDon’t just check the name of the person sending you the email. Check their email address by hovering your mouse over the ‘from’ address. Make sure no alterations (like additional numbers or letters) have been made. Check out the difference between these two email addresses as an example of altered emails: [email protected] [email protected] Just remember, this isn’t a foolproof method. Sometimes companies make use of unique or varied domains to send emails, and some smaller companies use third party email providers.
Sir/Madam? Also, what’s up with the 17 in the middle of the sentence?3. Legit companies have domain emailsDon’t just check the name of the person sending you the email. Check their email address by hovering your mouse over the ‘from’ address. Make sure no alterations (like additional numbers or letters) have been made. Check out the difference between these two email addresses as an example of altered emails: [email protected] [email protected] Just remember, this isn’t a foolproof method. Sometimes companies make use of unique or varied domains to send emails, and some smaller companies use third party email providers.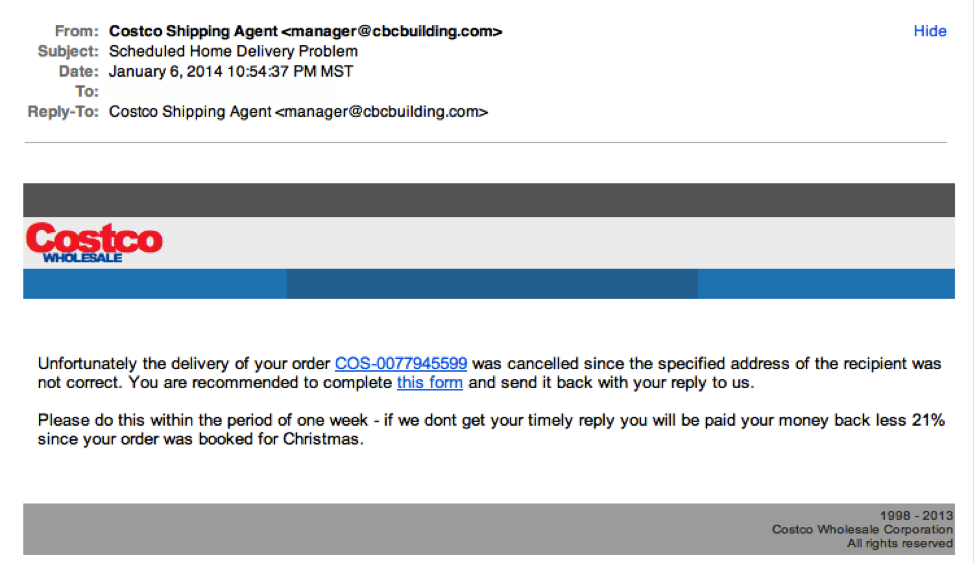 “Costco’s” logo is just a bit off. This is what the Costco logo is supposed to look like.
“Costco’s” logo is just a bit off. This is what the Costco logo is supposed to look like. See the difference? Subtle, no? 4. Legit companies know how to spellPossibly the easiest way to recognize a scammy email is bad grammar. An email from a legitimate organization should be well written. Little known fact – there’s actually a purpose behind bad syntax. Hackers generally aren’t stupid. They prey on the uneducated because they are easier targets.
See the difference? Subtle, no? 4. Legit companies know how to spellPossibly the easiest way to recognize a scammy email is bad grammar. An email from a legitimate organization should be well written. Little known fact – there’s actually a purpose behind bad syntax. Hackers generally aren’t stupid. They prey on the uneducated because they are easier targets.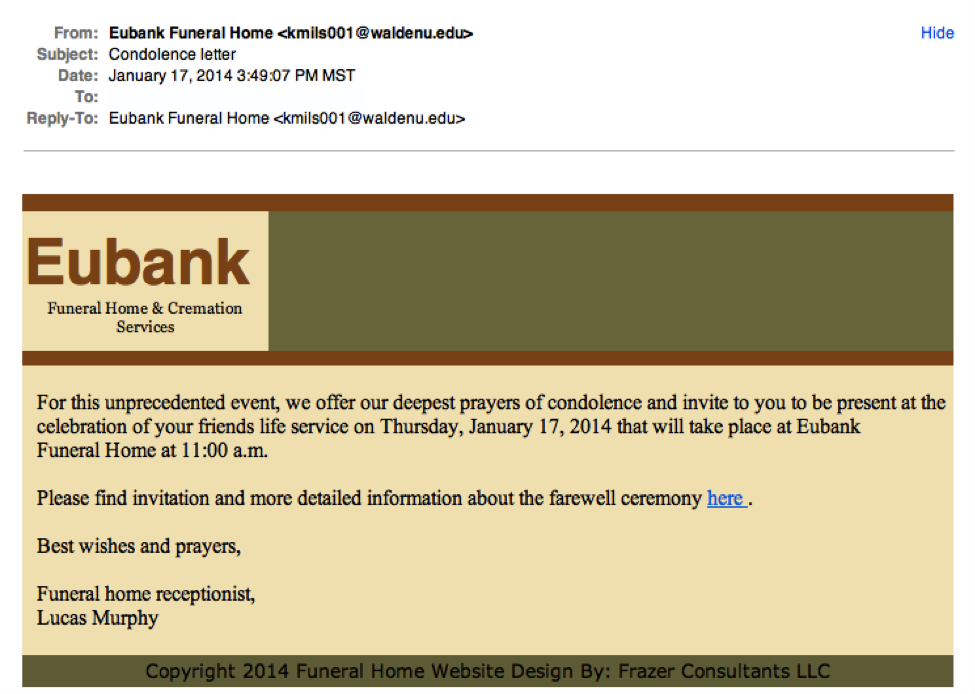 Notice the apostrophe in the word ‘friends’? Me neither. Other than that tiny grammar mistake, this is a very convincing email. 5. Legit companies don’t force you to their websiteSometimes phishing emails are coded entirely as a hyperlink. Therefore, clicking accidentally or deliberately anywhere in the email will open a fake web page, or download spam onto your computer.
Notice the apostrophe in the word ‘friends’? Me neither. Other than that tiny grammar mistake, this is a very convincing email. 5. Legit companies don’t force you to their websiteSometimes phishing emails are coded entirely as a hyperlink. Therefore, clicking accidentally or deliberately anywhere in the email will open a fake web page, or download spam onto your computer.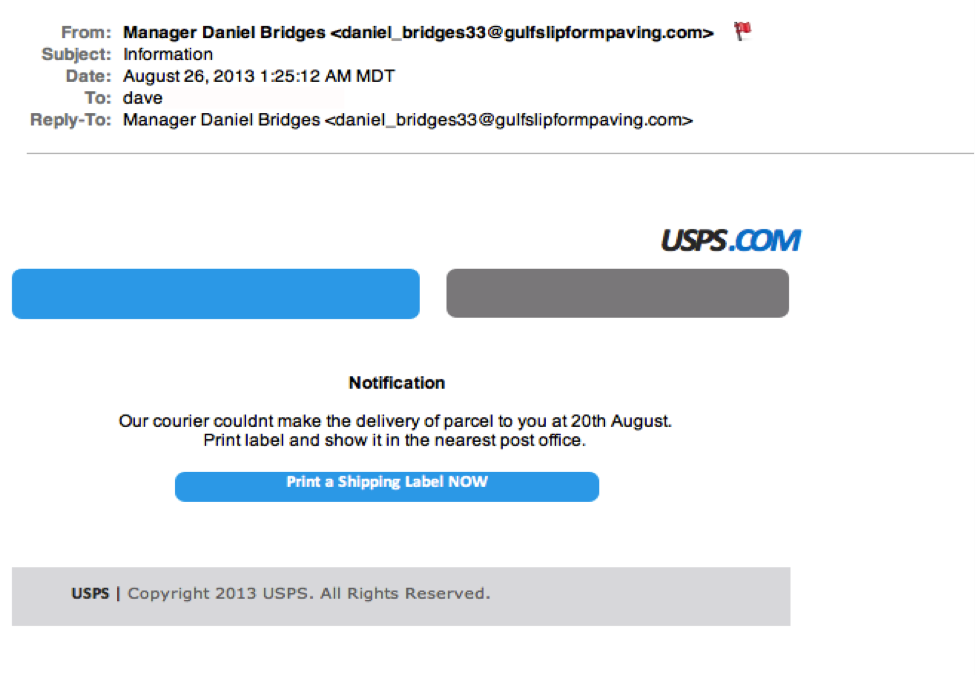 This whole email is likely a gigantic hyperlink. 6. Legit companies don’t send unsolicited attachmentsUnsolicited emails that contain attachments reek of hackers. Typically, authentic institutions don’t randomly send you emails with attachments, but instead direct you to download documents or files on their own website.
This whole email is likely a gigantic hyperlink. 6. Legit companies don’t send unsolicited attachmentsUnsolicited emails that contain attachments reek of hackers. Typically, authentic institutions don’t randomly send you emails with attachments, but instead direct you to download documents or files on their own website. ![]() Like the tips above, this method isn’t foolproof. Sometimes companies that already have your email will send you information, such as a white paper, that may require a download. In that case, be on the lookout for high-risk attachment file types include .exe, .scr, and .zip. (When in doubt, contact the company directly using contact information obtained from their actual website.)
Like the tips above, this method isn’t foolproof. Sometimes companies that already have your email will send you information, such as a white paper, that may require a download. In that case, be on the lookout for high-risk attachment file types include .exe, .scr, and .zip. (When in doubt, contact the company directly using contact information obtained from their actual website.)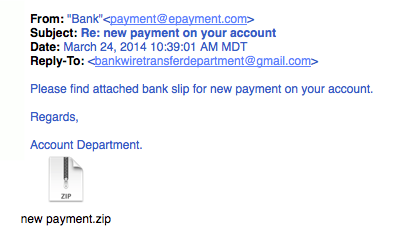 Just remember, curiosity killed the cat.7. Legit company links match legitimate URLsJust because a link says it’s going to send you to one place, doesn’t mean it’s going to. Double check URLs. If the link in the text isn’t identical to the URL displayed as the cursor hovers over the link, that’s a sure sign you will be taken to a site you don’t want to visit. If a hyperlink’s URL doesn’t seem correct, or doesn’t match the context of the email, don’t trust it. Ensure additional security by hovering your mouse over embedded links (without clicking!) and ensure the link begins with https://.
Just remember, curiosity killed the cat.7. Legit company links match legitimate URLsJust because a link says it’s going to send you to one place, doesn’t mean it’s going to. Double check URLs. If the link in the text isn’t identical to the URL displayed as the cursor hovers over the link, that’s a sure sign you will be taken to a site you don’t want to visit. If a hyperlink’s URL doesn’t seem correct, or doesn’t match the context of the email, don’t trust it. Ensure additional security by hovering your mouse over embedded links (without clicking!) and ensure the link begins with https://.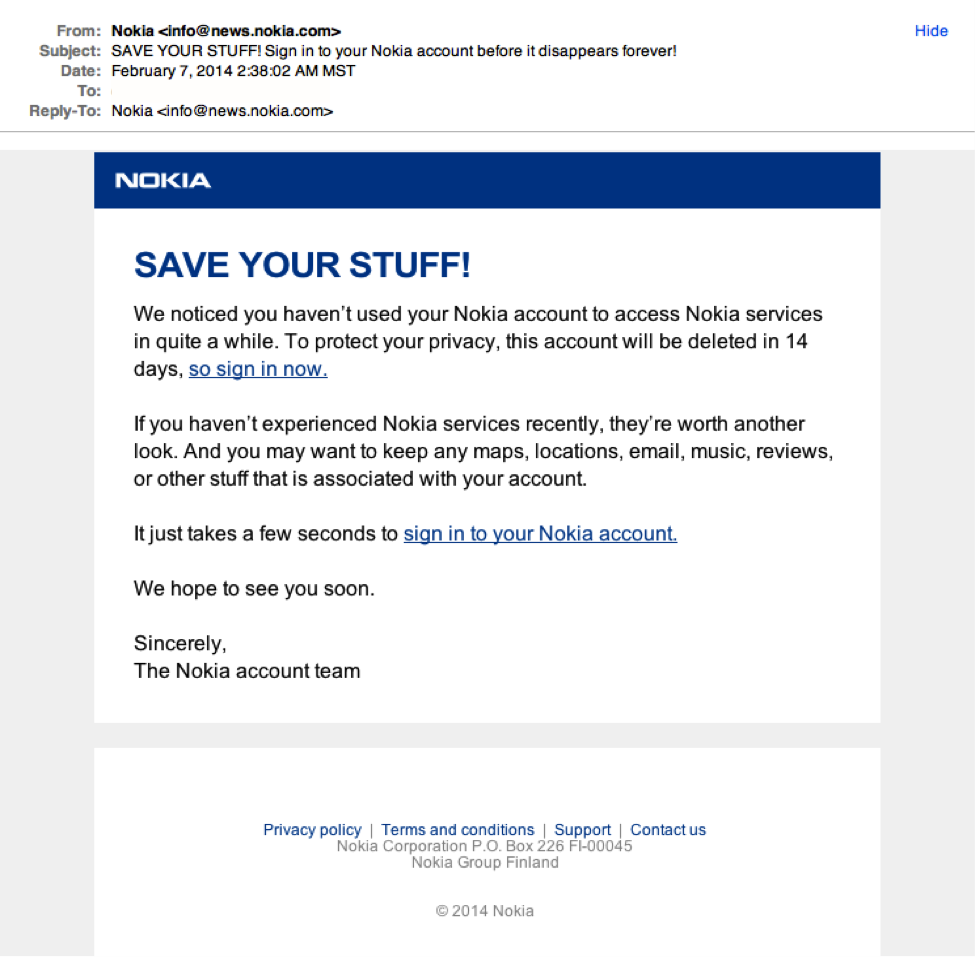 Although very convincing, the real Nokia wouldn’t be sending you a “Save your stuff” email from [email protected] doesn’t matter if you have the most secure security system in the world. It takes only one untrained employee to be fooled by a phishing attack and give away the data you’ve worked so hard to protect. Make sure both you and your employees understand the telltale signs of a phishing attempt.Was this post helpful? If so, please share!wistiaEmbed = Wistia.embed(“exi3oxmnof”); David Ellis (GCIH, QSA, PFI, CISSP) is Director of Forensic Investigations at SecurityMetrics with over 25 years of law enforcement and investigative experience. Check out his other blog posts.
Although very convincing, the real Nokia wouldn’t be sending you a “Save your stuff” email from [email protected] doesn’t matter if you have the most secure security system in the world. It takes only one untrained employee to be fooled by a phishing attack and give away the data you’ve worked so hard to protect. Make sure both you and your employees understand the telltale signs of a phishing attempt.Was this post helpful? If so, please share!wistiaEmbed = Wistia.embed(“exi3oxmnof”); David Ellis (GCIH, QSA, PFI, CISSP) is Director of Forensic Investigations at SecurityMetrics with over 25 years of law enforcement and investigative experience. Check out his other blog posts.
- 1
- 2
- 3
- 4
- Next Page »