After all, gullible employees lead to security breaches.  By: Brand BarneyHumans want to trust other humans. If I struck up a conversation with a gentleman in a suit at the bus stop who explained his life story, why would I distrust him? We all have a natural tendency to believe what trustworthy-looking people tell us. And that’s what gets us in trouble.
By: Brand BarneyHumans want to trust other humans. If I struck up a conversation with a gentleman in a suit at the bus stop who explained his life story, why would I distrust him? We all have a natural tendency to believe what trustworthy-looking people tell us. And that’s what gets us in trouble.![]() Tweet
Tweet What is social engineering?Social engineering is a way of manipulating people socially so that they trust the social engineer and eventually provide some sort of useable data. For instance, instead of trying to find software vulnerabilities to exploit for sensitive data, a social engineer might try to trick someone into divulging an administrative password without realizing it.Have you ever seen the crime drama Catch Me If You Can? Frank Abagnale, the main character, is a master of social engineering. He convinces people he’s an airline pilot, doctor, and attorney by forging documents and acting like he belongs. The scary thing is, it’s a true story.What’s the problem with social engineering?
What is social engineering?Social engineering is a way of manipulating people socially so that they trust the social engineer and eventually provide some sort of useable data. For instance, instead of trying to find software vulnerabilities to exploit for sensitive data, a social engineer might try to trick someone into divulging an administrative password without realizing it.Have you ever seen the crime drama Catch Me If You Can? Frank Abagnale, the main character, is a master of social engineering. He convinces people he’s an airline pilot, doctor, and attorney by forging documents and acting like he belongs. The scary thing is, it’s a true story.What’s the problem with social engineering?
© SecurityMetrics | www.securitymetrics.com/pci | 801.705.5665 |
Hey guys and welcome back to the SecurityQ, your source for business data security Today on the SecurityQ, we’re back with part two of social engineering. Alright guys. Last time on the SecurityQ, we talked a little about social engineering and I showed you a pretty sweet example. But today I interviewed two security experts: an auditor and forensics investigator. Here’s what they had to say about social engineering. Social engineering, the part that frustrated us was how easy it was to do this with customers. We’d say, hey we’re here to work on your network or work on your computers, can you show me to your server room? And they’d lead us right back there. They wouldn’t ask us, you should know the password, and I’m gonna give it to you. They’d just give us the password. We would send a letter later on and tell them how easy it was to get inside. They’re always quite surprised. Usually when you go to a company they feel like their people are trained very well. I’ve worked at customer sites where they’ve been really secure and they’ve done a much better job. Bu by far, most companies are lax on their rules and people need better training. There’s another way that it’s kind of unusual. That merchants really need to be on guard for the social engineer. For example, there was a an investigation we were involved in where this guy had very limited IT skills, but he knew how to talk. He simply opened up the yellow pages and started calling all the restaurants in a particular chain that were in this area. He said, I have to do some system maintenance and I can walk you right through it. We’ll do it together over the phone. Enabled a remote session with them, and virtually while he was on the phone with the manager, installed malware. Alright guys, I’ve said it before and I’m gonna say it again. You may have the best technology on the face of the planet, but if you don’t protect yourself from the social threat, you’re leaving your business wide open. Our advice? Train your employees against the social threat and remember to always prepare because your security matters. Well guys that’s all the time we have today on the SecurityQ. But as always, we want to hear from you. So post your questions in the comments below and don’t forget to subscribe. See ya next time on the SecurityQ.wistiaEmbed = Wistia.embed(“5mi8u7k6kc”); Here are some common ways social engineers try to socially engineer us Steal badges and credentials in unlocked carsGo to the local donation store and buy old company T-shirtsPose as janitorial staff to get into a building“Can you hold the door for me? I don’t have my badge.”Pose as an IT person that needs to fix the networkTry unlocked doors around the backside of buildings Pose as law enforcement conducting an inspection Dumpster dive for sensitive documents![]() Here’s what happens when I try to socially engineer someone.
Here’s what happens when I try to socially engineer someone.
© SecurityMetrics | www.securitymetrics.com/pci | 801.705.5665 |
Hey guys, welcome back to the SecurityQ, your source for business data security. Today on the SecurityQ, we’re gonna discuss one topic. The social threat to your business. Here’s the game if you don’t mind if I try. Out of the things you have inside, would you say would be most valuable? The thing inside your pockets We’ll take your front pocket here, do you have something inside? You don’t mind if I bring this out in public do you? I believe that’s really strange. So you have anything else? Okay guys, so we just saw a pretty sweet video of a social engineer, or a con man, stealing personal items from a guy. I have to tell you I’m quite impressed with his skill. Now a lot of businesses ask me, what is a social engineer and how does that apply to my business? The truth is, a social engineer is somebody that uses social interaction to steal data. It could be personal, that data could be physical, that data could be coming from your trash can. It’s data they want. And they’re gonna use any and all tactics to get that data. Now I’m gonna show you what social engineering looks like at an actual business and I’m personally going to do it. Jive Communications, Voice over IP made affordable and reliable, has graciously given us permission to run a simulation. Everyone involved is an actor. Hi how are you? My name is Brandon Barney and I’m the IT director upstairs. I was monitoring our logs this weekend, and it looked like your Wi-Fi was bleeding into ours. If I could jump onto your computer systems real quick and make sure that’s not the case, I’d sure appreciate it. This employee has one have two choices. They’re either going completely fold and give me access to the network, or they’re gonna shut me down. The question is, what are you and your employees going to do? If you’re looking for information or tactics used by these criminals, check out the link for information from PC world. Our advice? Train your employees and test them. There are lots of professionals out there that can assist you in doing this. Remember, your security matters. Well guys, that’s all the time we have for today on the SecurityQ. If you’re looking for detailed information on social engineering, I’m going to be posting a pretty sweet video response. Remember, we want to hear from you so post your questions in the comments below, and don’t forget to subscribe. See you next time on the SecurityQ.wistiaEmbed = Wistia.embed(“deuhcjmzzj”); How to avoid being a victim of social engineeringThe best way to avoid being socially engineered is by educating yourself and your employees. Here are some points you should touch on during training:You should be slightly paranoid (better to be safe than sorry)Social engineers don’t sneak around. They’re confident and friendly. They look like they belong. Don’t be pressured by their convincing ways.Never give out your username/password, badge, PIN, ID number, credit card, or schedule. In essence, never give out sensitive information about you or your company.Ask for a contact to verify why the person needs the information they’re asking forDon’t hold secure doors open for people you don’t knowThe only way to identify if your employees have soaked in all that social engineering knowledge is to test them. You can don a disguise and test them yourself, or enlist the help of a social engineering professional (also called a pen tester), to come onsite and test your employees, experiment with your physical security, and see what interesting information they can find in your trash cans.Have a business security question? Tweet me and you may see your question answered on the next SecurityQ.Brand Barney (CISSP) is an Associate Security Analyst at SecurityMetrics and has over 10 years of compliance, data security, and database management experience. Follow him on Twitter and check out his other blog posts.
 After all, gullible employees lead to security breaches.
After all, gullible employees lead to security breaches. 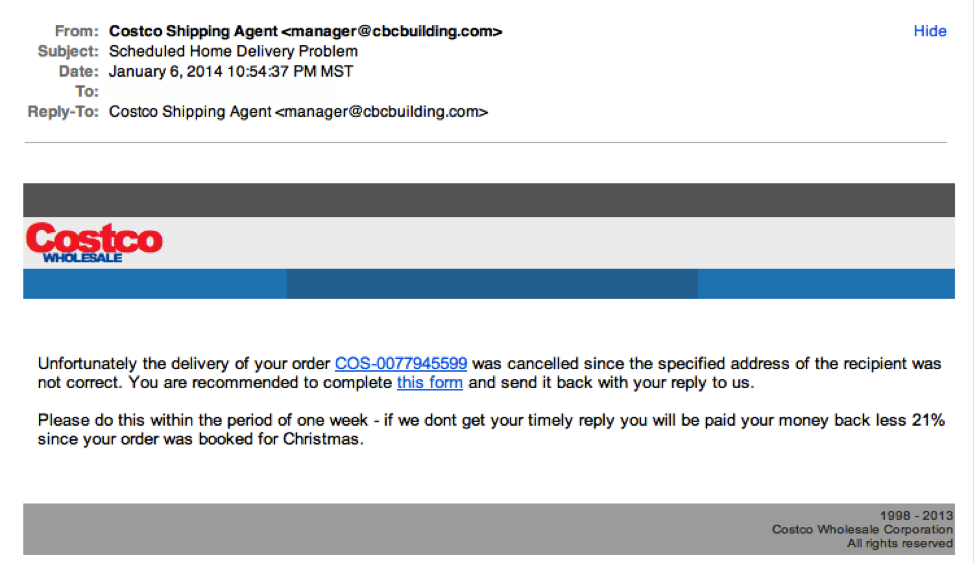 “You can fool some of the people all of the time, and all of the people some of the time, but you cannot fool all of the people all of the time.” –Abraham Lincoln
“You can fool some of the people all of the time, and all of the people some of the time, but you cannot fool all of the people all of the time.” –Abraham Lincoln  By: David EllisAre you sure that email from UPS is actually from UPS? (Or Costco, BestBuy, or the myriad of unsolicited emails you receive every day?) Companies and individuals are often targeted by cybercriminals via emails designed to look like they came from a legitimate bank, government agency, or organization. In these emails, the sender asks recipients to click on a link that takes them to a page where they will confirm personal data, account information, etc.
By: David EllisAre you sure that email from UPS is actually from UPS? (Or Costco, BestBuy, or the myriad of unsolicited emails you receive every day?) Companies and individuals are often targeted by cybercriminals via emails designed to look like they came from a legitimate bank, government agency, or organization. In these emails, the sender asks recipients to click on a link that takes them to a page where they will confirm personal data, account information, etc. 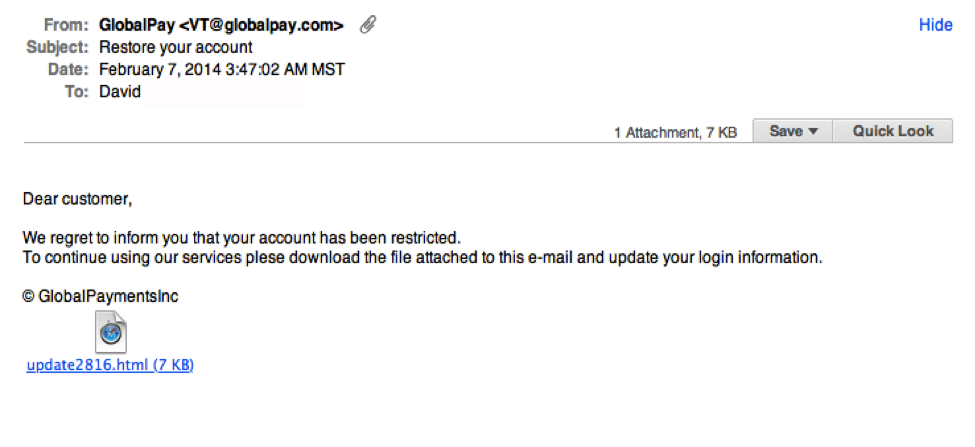 Notice the generic salutation at the beginning, and the unsolicited web link attachment?2. Legit companies call you by your namePhishing emails typically use generic salutations such as “Dear valued member,” “Dear account holder,” or “Dear customer.” If a company you deal with required information about your account, the email would call you by name and probably direct you to contact them via phone.
Notice the generic salutation at the beginning, and the unsolicited web link attachment?2. Legit companies call you by your namePhishing emails typically use generic salutations such as “Dear valued member,” “Dear account holder,” or “Dear customer.” If a company you deal with required information about your account, the email would call you by name and probably direct you to contact them via phone. Sir/Madam? Also, what’s up with the 17 in the middle of the sentence?3. Legit companies have domain emailsDon’t just check the name of the person sending you the email. Check their email address by hovering your mouse over the ‘from’ address. Make sure no alterations (like additional numbers or letters) have been made. Check out the difference between these two email addresses as an example of altered emails:
Sir/Madam? Also, what’s up with the 17 in the middle of the sentence?3. Legit companies have domain emailsDon’t just check the name of the person sending you the email. Check their email address by hovering your mouse over the ‘from’ address. Make sure no alterations (like additional numbers or letters) have been made. Check out the difference between these two email addresses as an example of altered emails:  See the difference? Subtle, no? 4. Legit companies know how to spellPossibly the easiest way to recognize a scammy email is bad grammar. An email from a legitimate organization should be well written. Little known fact – there’s actually a purpose behind bad syntax. Hackers generally aren’t stupid. They prey on the uneducated because they are easier targets.
See the difference? Subtle, no? 4. Legit companies know how to spellPossibly the easiest way to recognize a scammy email is bad grammar. An email from a legitimate organization should be well written. Little known fact – there’s actually a purpose behind bad syntax. Hackers generally aren’t stupid. They prey on the uneducated because they are easier targets.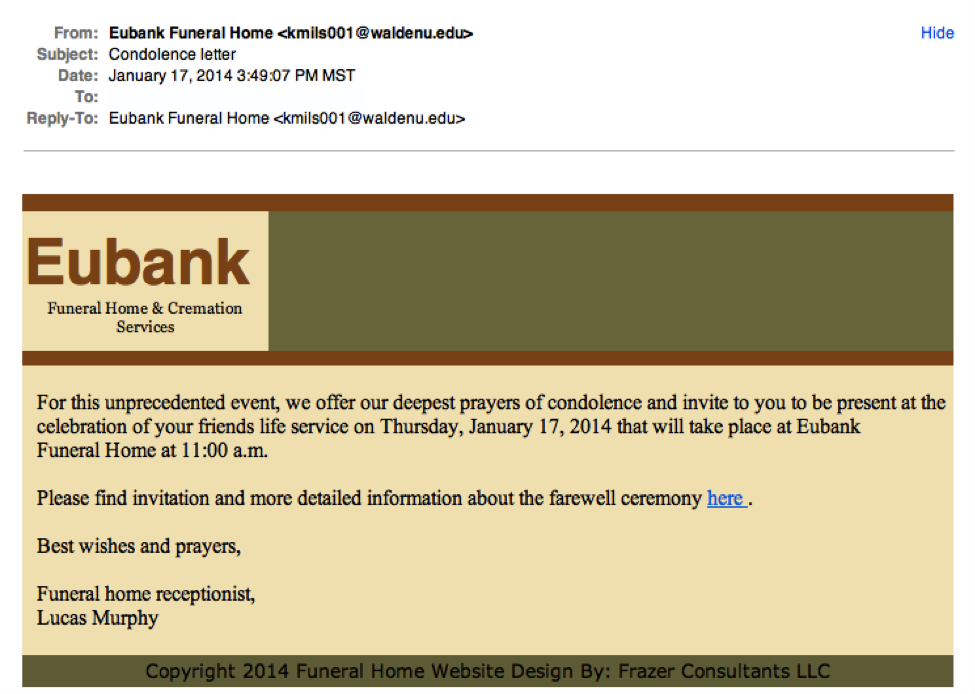 Notice the apostrophe in the word ‘friends’? Me neither. Other than that tiny grammar mistake, this is a very convincing email. 5. Legit companies don’t force you to their websiteSometimes phishing emails are coded entirely as a hyperlink. Therefore, clicking accidentally or deliberately anywhere in the email will open a fake web page, or download spam onto your computer.
Notice the apostrophe in the word ‘friends’? Me neither. Other than that tiny grammar mistake, this is a very convincing email. 5. Legit companies don’t force you to their websiteSometimes phishing emails are coded entirely as a hyperlink. Therefore, clicking accidentally or deliberately anywhere in the email will open a fake web page, or download spam onto your computer.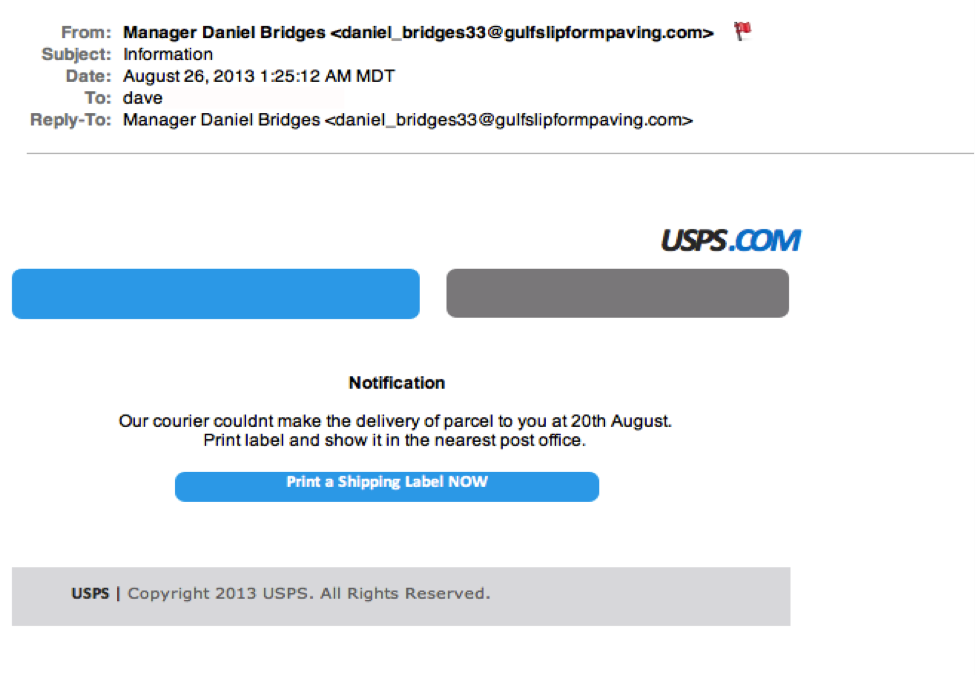 This whole email is likely a gigantic hyperlink. 6. Legit companies don’t send unsolicited attachmentsUnsolicited emails that contain attachments reek of hackers. Typically, authentic institutions don’t randomly send you emails with attachments, but instead direct you to download documents or files on their own website.
This whole email is likely a gigantic hyperlink. 6. Legit companies don’t send unsolicited attachmentsUnsolicited emails that contain attachments reek of hackers. Typically, authentic institutions don’t randomly send you emails with attachments, but instead direct you to download documents or files on their own website. 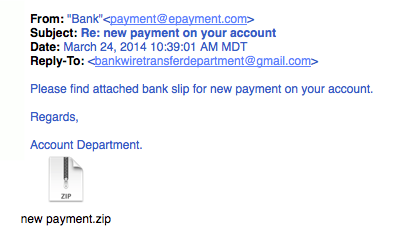 Just remember, curiosity killed the cat.7. Legit company links match legitimate URLsJust because a link says it’s going to send you to one place, doesn’t mean it’s going to. Double check URLs. If the link in the text isn’t identical to the URL displayed as the cursor hovers over the link, that’s a sure sign you will be taken to a site you don’t want to visit. If a hyperlink’s URL doesn’t seem correct, or doesn’t match the context of the email, don’t trust it. Ensure additional security by hovering your mouse over embedded links (without clicking!) and ensure the link begins with https://.
Just remember, curiosity killed the cat.7. Legit company links match legitimate URLsJust because a link says it’s going to send you to one place, doesn’t mean it’s going to. Double check URLs. If the link in the text isn’t identical to the URL displayed as the cursor hovers over the link, that’s a sure sign you will be taken to a site you don’t want to visit. If a hyperlink’s URL doesn’t seem correct, or doesn’t match the context of the email, don’t trust it. Ensure additional security by hovering your mouse over embedded links (without clicking!) and ensure the link begins with https://.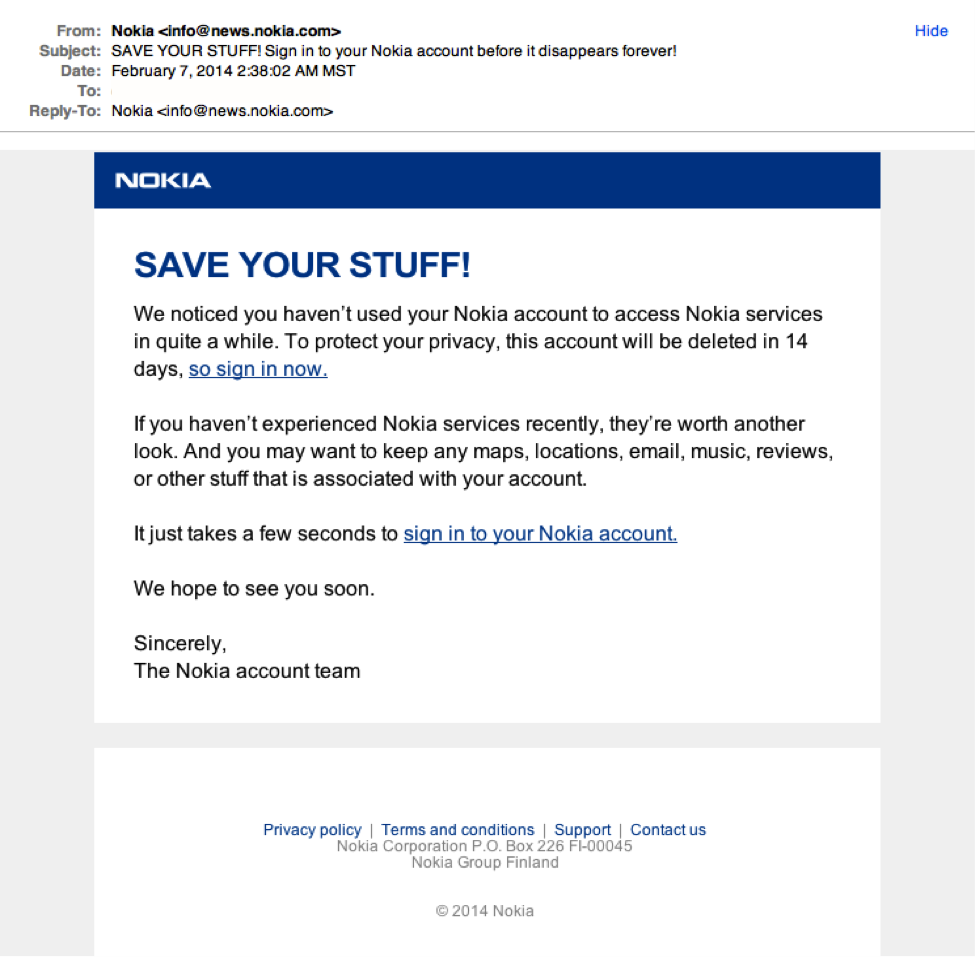 Although very convincing, the real Nokia wouldn’t be sending you a “Save your stuff” email from
Although very convincing, the real Nokia wouldn’t be sending you a “Save your stuff” email from 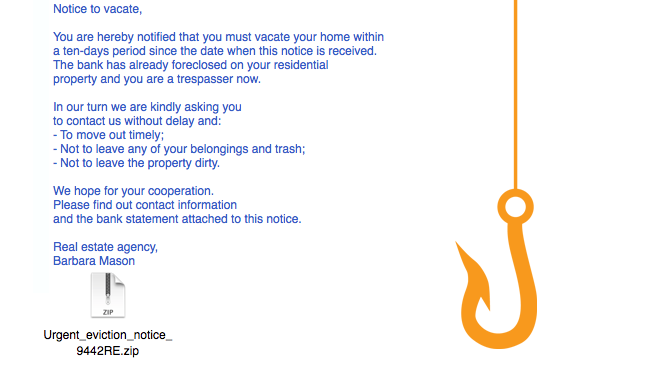 Criminals have countless methods to trick email users.
Criminals have countless methods to trick email users.  This is achieved through a few different methods. Sometimes, cybercriminals trick email recipients into opening an email attachment that loads harmful malware onto their system. Other times, they trick recipients into providing sensitive personal information directly via web forms. Either way, these seemingly teeny mistakes could make serious ripples across your organization, compromising either corporate or personal security.SEE ALSO: 7 Ways to Recognize a Phishing Email.Typically, phishers send legitimate-looking emails that appear as though they originated from reputable companies that many people do business with like BestBuy, Amazon, Federal Express, DHL, and PayPal. The emails often ask customers to confirm information or to go to the business site by clicking on a provided link, and often include a statement of impending consequences if you fail to act.Here are a few common ploys cybercriminals use to trick you.1. The Government ManeuverThis type of email looks like it originated from a federal body, such as the FBI, and tries to scare you into providing your information. Common messages include, ‘Your insurance has been denied because of incomplete information. Click here to provide your information.’ Or, ‘Because you illegally downloaded files, your Internet access will be revoked until you enter the requested information in the form below.’
This is achieved through a few different methods. Sometimes, cybercriminals trick email recipients into opening an email attachment that loads harmful malware onto their system. Other times, they trick recipients into providing sensitive personal information directly via web forms. Either way, these seemingly teeny mistakes could make serious ripples across your organization, compromising either corporate or personal security.SEE ALSO: 7 Ways to Recognize a Phishing Email.Typically, phishers send legitimate-looking emails that appear as though they originated from reputable companies that many people do business with like BestBuy, Amazon, Federal Express, DHL, and PayPal. The emails often ask customers to confirm information or to go to the business site by clicking on a provided link, and often include a statement of impending consequences if you fail to act.Here are a few common ploys cybercriminals use to trick you.1. The Government ManeuverThis type of email looks like it originated from a federal body, such as the FBI, and tries to scare you into providing your information. Common messages include, ‘Your insurance has been denied because of incomplete information. Click here to provide your information.’ Or, ‘Because you illegally downloaded files, your Internet access will be revoked until you enter the requested information in the form below.’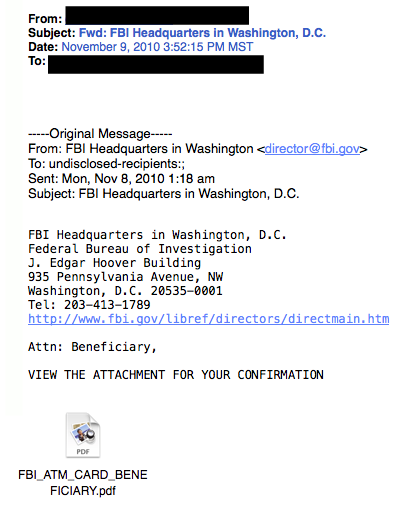 2. The Friend TacticIf an unknown individual claims to know you in an email, you are probably not suffering from amnesia. More than likely, it is an attempt to get you to wire him/her money. A variation on this theme is that one of your known friends is in a foreign country and needs your help. Before you send your ‘friend’ money, give them a call to verify. Your true friend’s email contact list was probably hijacked.
2. The Friend TacticIf an unknown individual claims to know you in an email, you are probably not suffering from amnesia. More than likely, it is an attempt to get you to wire him/her money. A variation on this theme is that one of your known friends is in a foreign country and needs your help. Before you send your ‘friend’ money, give them a call to verify. Your true friend’s email contact list was probably hijacked.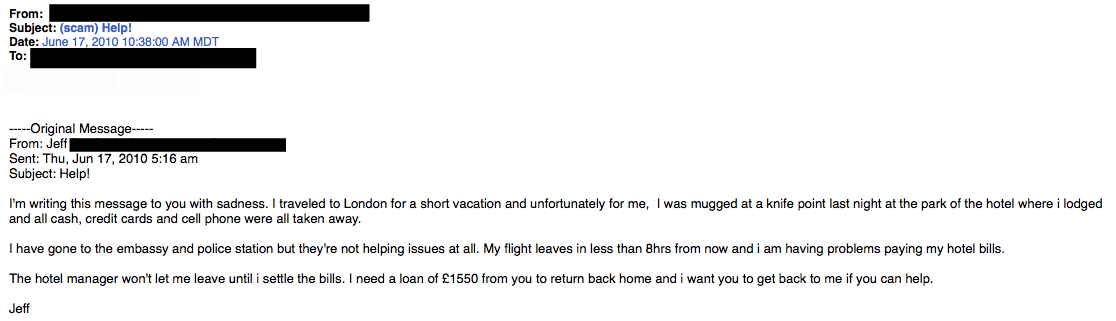 3. The Billing ProblemThis phishing tactic is tricky because it appears quite legitimate. This email states that an item you purchased online cannot be shipped to you because the credit card was expired (or billing address wasn’t correct, etc.). If you click on the provided link, it takes you to a spoofed website and asks for updated payment/shipping information, etc.
3. The Billing ProblemThis phishing tactic is tricky because it appears quite legitimate. This email states that an item you purchased online cannot be shipped to you because the credit card was expired (or billing address wasn’t correct, etc.). If you click on the provided link, it takes you to a spoofed website and asks for updated payment/shipping information, etc.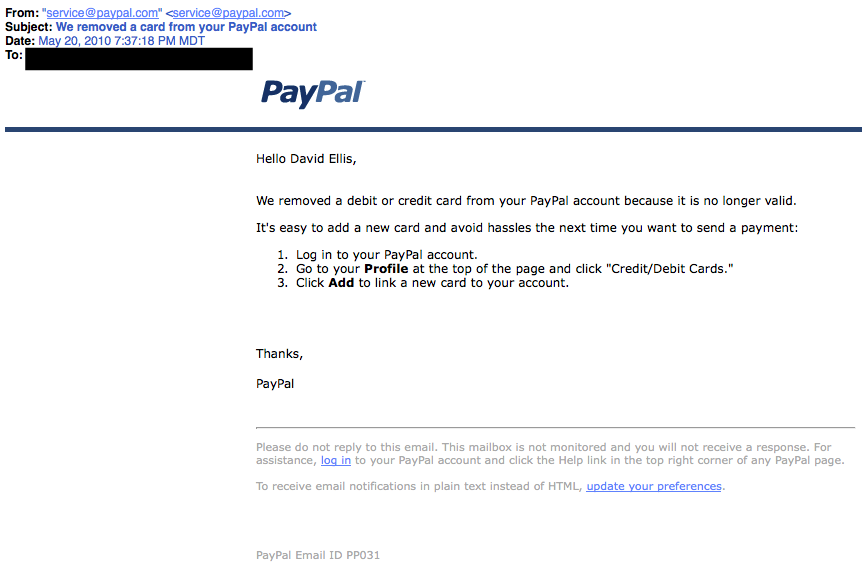 A lot of folks have personal and business PayPal accounts. Here, notice that the email header is from
A lot of folks have personal and business PayPal accounts. Here, notice that the email header is from 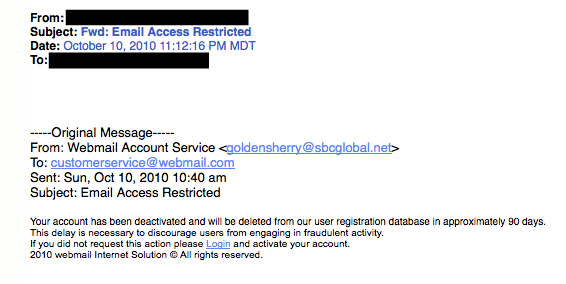 5. The Virus ScareThis type of email states that your computer has been infected! In order to avoid losing your data and infecting your computer the email instructs you to follow the provided link, or download the “anti-virus” attachment.
5. The Virus ScareThis type of email states that your computer has been infected! In order to avoid losing your data and infecting your computer the email instructs you to follow the provided link, or download the “anti-virus” attachment.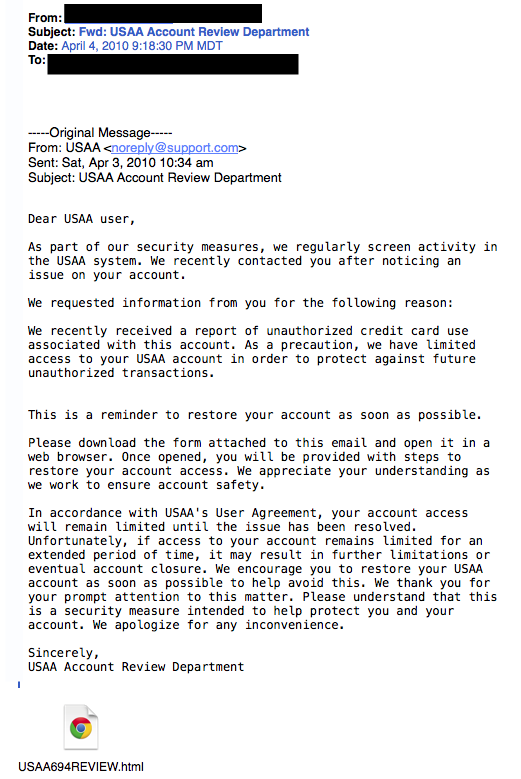 Whatever you do, DON’T CLICK ON THE LINK!6. The Contest WinnerDon’t get too excited when you receive emails that claim you’ve won something, or received an inheritance from a relative you’ve never heard of. 99.9% of the time, these are absolutely bogus. To claim your prize, the email requires you click a link and enter your info for prize shipment.
Whatever you do, DON’T CLICK ON THE LINK!6. The Contest WinnerDon’t get too excited when you receive emails that claim you’ve won something, or received an inheritance from a relative you’ve never heard of. 99.9% of the time, these are absolutely bogus. To claim your prize, the email requires you click a link and enter your info for prize shipment.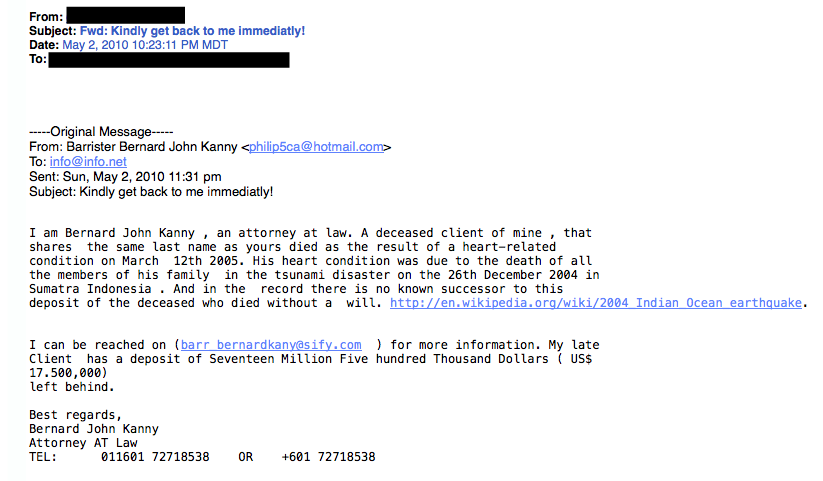 7. The Friendly BankYour bank may offer account notifications when certain amounts are withdrawn from your accounts. This ploy tricks you with a fake account notification stating that an amount has been withdrawn from your account that exceeds your notification limit. If you have any questions about this withdrawal (which you probably would), it gives you a convenient link that leads to a web form asking for your bank account number “for verification purposes.” Instead of clicking on the link, give your bank a call. They may want to take action on the malicious email.
7. The Friendly BankYour bank may offer account notifications when certain amounts are withdrawn from your accounts. This ploy tricks you with a fake account notification stating that an amount has been withdrawn from your account that exceeds your notification limit. If you have any questions about this withdrawal (which you probably would), it gives you a convenient link that leads to a web form asking for your bank account number “for verification purposes.” Instead of clicking on the link, give your bank a call. They may want to take action on the malicious email.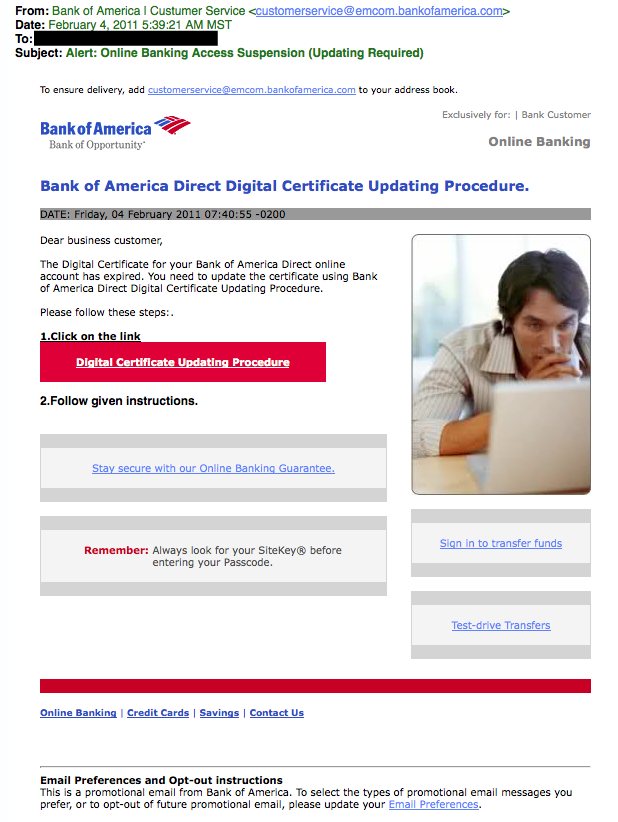 Due to the graphics and opt-out instructions, this phishing attempt seems very legitimate.8. The VictimBeing wrongly accused of something doesn’t feel good. This type of phishing email acts as an angry customer whom supposedly sent you money in return for a shipped product. The email concludes with the threat that they will inform the authorities if they don’t hear from you.
Due to the graphics and opt-out instructions, this phishing attempt seems very legitimate.8. The VictimBeing wrongly accused of something doesn’t feel good. This type of phishing email acts as an angry customer whom supposedly sent you money in return for a shipped product. The email concludes with the threat that they will inform the authorities if they don’t hear from you.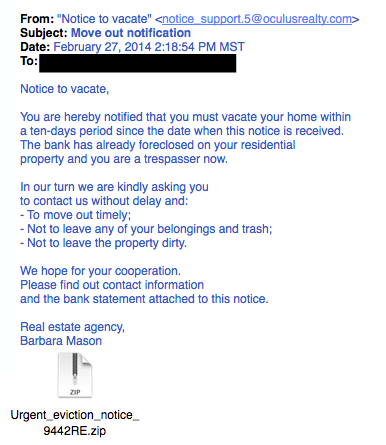 This is another type of victim scam. Who wouldn’t be a little worried after receiving this email?9. The Tax CommunicationPractically everyone has annual taxes to submit. That’s why this phishing attempt is so popular. The message states that you are either eligible to receive a tax refund, or you have been selected to be audited. It then requests that you submit a tax refund request or tax form.
This is another type of victim scam. Who wouldn’t be a little worried after receiving this email?9. The Tax CommunicationPractically everyone has annual taxes to submit. That’s why this phishing attempt is so popular. The message states that you are either eligible to receive a tax refund, or you have been selected to be audited. It then requests that you submit a tax refund request or tax form.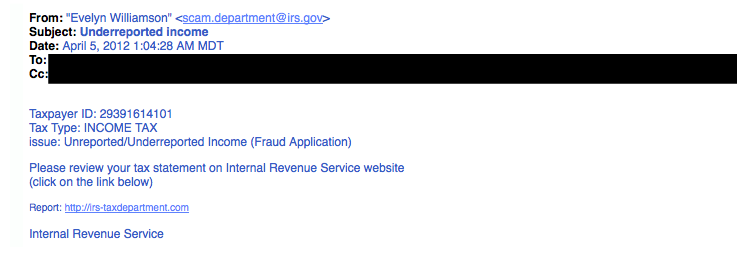 10. The CheckupThis is one of the more unassuming phishing email attempts. It claims [company name] is conducting a routine security procedure and requests you verify your account by providing information. This scam is especially effective if you happen to be a customer of the named business.
10. The CheckupThis is one of the more unassuming phishing email attempts. It claims [company name] is conducting a routine security procedure and requests you verify your account by providing information. This scam is especially effective if you happen to be a customer of the named business.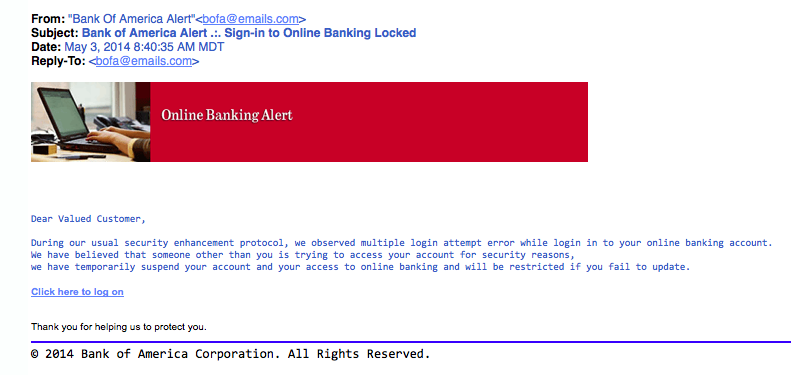 If you receive a phishing email:Don’t click on any links, open attachments, or expand any included picturesDon’t try to reply to the senderReport the scam (forward the e-mail to the FTC –
If you receive a phishing email:Don’t click on any links, open attachments, or expand any included picturesDon’t try to reply to the senderReport the scam (forward the e-mail to the FTC –